2021 was the year of records, top results and partnerships.
Our captain changed again. We had gnx (ELT founder) as captain from the team beginning until 2019. In 2020 the position was occupied by n0ps13d . This year, andre_smaira assumed the captain position.
In 2021 we created the ELT instagram, where you can find our news and a lot of material for study, and we put all of our important links together in linktree to turn it easy for our followers to always find any ELT information in an easy way. We also created in our website a place where all of Pwn2Win (since de first one in 2014) challenges and write-ups can be found (if you could not find any of them, let us know).
We also started a new partnership with Mente Binária, where we monthly publish infosec introductory Portuguese articles for those who are starting their studies in the infosec field (contact us on social networks if you want a specific subject).
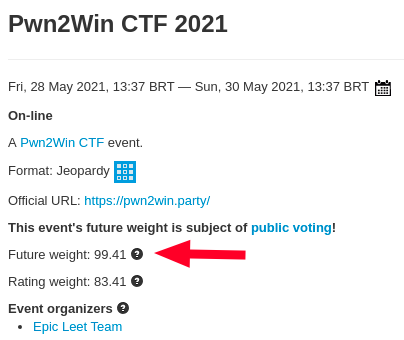
Pwn2win 2021 was amazing! The Pwn2Win of records! This year we got the largest sponsorship, both in value and number of partners! The event was honored with the registration of 1091 international teams and with the participation of top teams fighting for the last spot in the DEF CON CTF 2021. Yes! Pwn2Win 2021 was the first Brazilian CTF chosen to be DEF CON CTF Pre-Qualifier (https://oooverflow.io/dc-ctf-2021-quals/)!. As a result, the weight of the event in 2022 will be even greater (99.41 / 100), the fourth-highest for 2022. Less than 10 events have already had weights greater than 99 in all history of CTFTime! See here the Pwn2Win 2021 backstage for more details.
The team got 3 new and talented members (https://epicleet.team/line-up).
Just like last year, in 2021, unfortunately, we were unable to meet in person due to the Covid-19 pandemic that has yet to end. We hope that it will be possible to play at least one CTF spatially together or to meet at least at H2HC, which was canceled again this year.
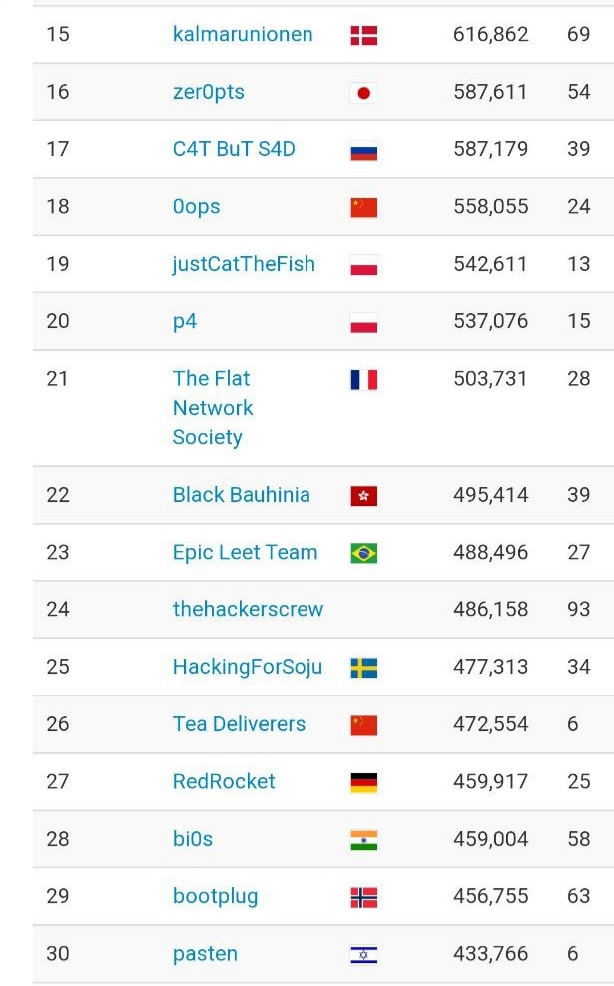
We had excellent results in CTFs again! We got the top 20 positions or better in 11 of the 26 CTFs we played, highlighting 4 of them weighed 90% or better. We beat the previous year’s result in 4 of those we also played in 2020 and played 12 CTFs that we didn’t play in 2020 in an attempt to choose higher-level CTFs. This had an excellent impact on our final ranking on the CTFTime worldwide scoreboard. We ended up closing the year in international 23rd place near, and sometimes better than, internationally known teams. It is also important to highlight that we maintained the Brazilian 1st place, a position we hold since 2014 (the year that the team joined on CTFTime).
After a year of hard work, we can celebrate our achievements, reflect on what can be improved and recharge our batteries for the challenges that will come in 2022. Happy holidays! We wish that next year will bring even more interesting challenges, make the good news more frequent and motivate the fight for more success for everyone.